Kubernetes Compliance Mapping: DevSecOps Guide
Kubernetes compliance can be complex, but integrating it into your DevSecOps pipeline makes it manageable. Here’s the gist:
- Why It Matters: Compliance frameworks like SOC 2, PCI DSS, and HIPAA are mandatory for securing Kubernetes environments. Ignoring them risks breaches, audit failures, and high costs.
- Key Challenges: Kubernetes’ dynamic nature – ephemeral pods, configuration drift, and API vulnerabilities – makes traditional audits ineffective.
- Solutions:
- Policy as Code (PaC): Automate compliance enforcement using tools like OPA Gatekeeper or Kyverno.
- Admission Controllers: Block non-compliant deployments in real-time.
- Continuous Monitoring: Use tools like Trivy and kube-bench for ongoing scans.
- CI/CD Integration: Shift-left scanning catches issues early with tools like Trivy and Checkov.
- Runtime Security: Detect live threats using tools like Falco.
Key Takeaway: Automating compliance ensures continuous security and reduces operational costs, making Kubernetes environments safer and audit-ready.
Kubernetes and DevSecOps Securing Deployments at Scale
sbb-itb-f9e5962
Key Compliance Frameworks for Kubernetes
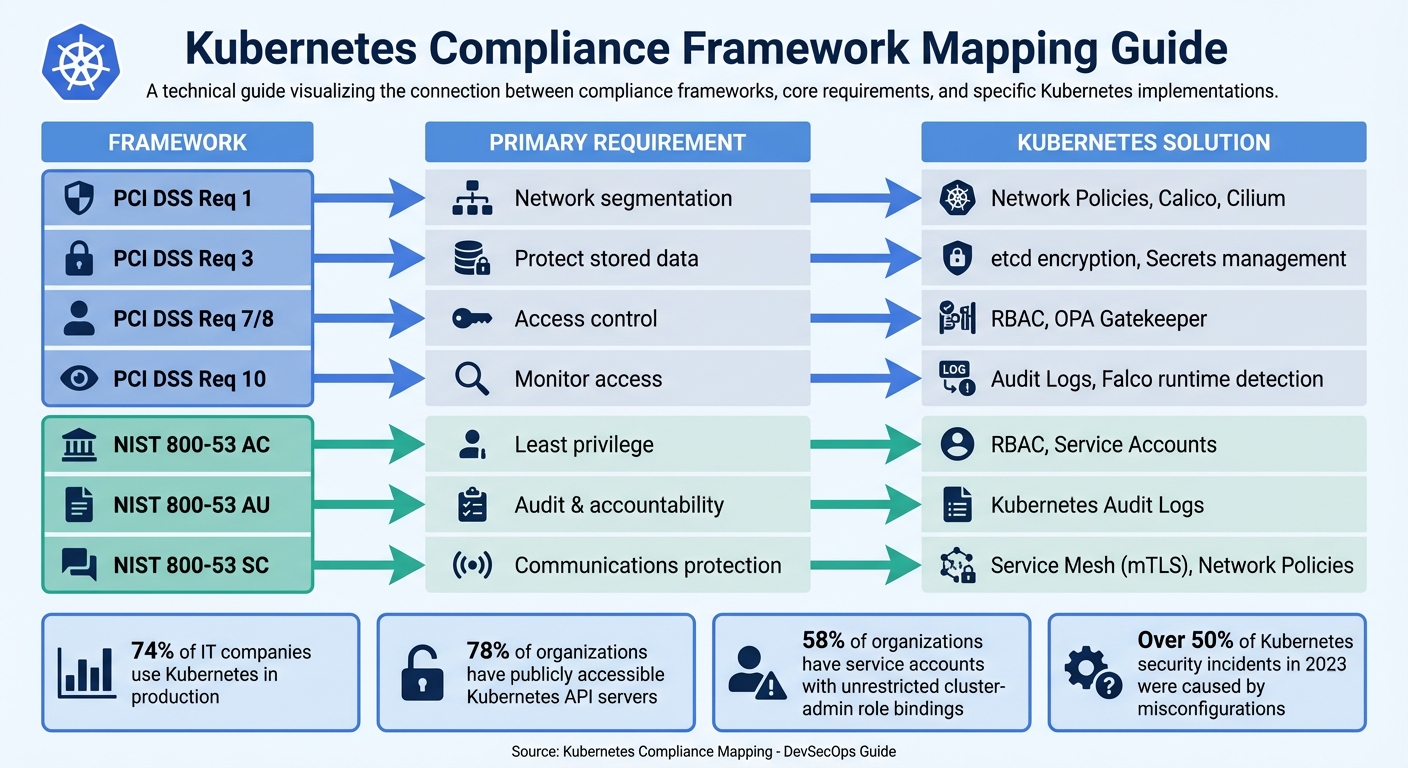
Kubernetes Compliance Framework Mapping Guide
Major Compliance Standards Explained
With Kubernetes powering 74% of IT companies’ production environments, compliance frameworks are critical for securing containerized workloads and meeting regulatory demands. These frameworks generally fall into two categories: security hardening benchmarks and regulatory compliance standards.
The CIS Kubernetes Benchmark offers detailed, community-driven guidelines for securing Kubernetes clusters. It organizes recommendations into two levels: Level 1, which focuses on practical measures with immediate security benefits, and Level 2, which provides advanced defenses for high-stakes environments. For organizations managing sensitive data, NIST SP 800-190 (Application Container Security Guide) outlines risks like image vulnerabilities, inadequate isolation, and host OS exploits, covering the container lifecycle from image creation to runtime.
Regulatory frameworks also play a significant role. For instance, PCI DSS enforces strict rules around network segmentation, data encryption, and access controls for systems handling payment card information. SOC 2 focuses on Trust Services Criteria, including Security, Availability, and Privacy. Meanwhile, government contractors face additional requirements under FedRAMP and CMMC, while the NSA-CISA Hardening Guide details best practices like pod security, network isolation, authentication, and audit logging.
"Though security and compliance are often mistaken as two separate requirements, their objectives are the same."
- Jonathan Kaftzan, ARMO
The MITRE ATT&CK for Kubernetes framework provides a unique perspective by cataloging adversary tactics and techniques, such as initial access and lateral movement. This knowledge helps organizations build threat models and strengthen their security posture by understanding how attackers exploit Kubernetes environments.
Together, these frameworks help translate broad compliance requirements into actionable steps within Kubernetes environments.
Converting Standards Into Kubernetes Controls
Kubernetes solutions excel at turning regulatory requirements into specific, enforceable controls. For example, network segmentation (a key PCI DSS Requirement 1) can be achieved using Kubernetes Network Policies to isolate workloads and enforce a "deny-all" default traffic rule. Similarly, data encryption requirements like PCI DSS Requirement 3 and GDPR can be addressed by enabling encryption at rest for etcd, managing sensitive keys with Kubernetes Secrets, and using mutual TLS (mTLS) through service meshes like Istio or Linkerd.
Access control is managed through Role-Based Access Control (RBAC), ensuring that users and service accounts only have permissions aligned with their roles. Audit logging, required by frameworks like FedRAMP and PCI DSS Requirement 10, can be implemented by enabling Kubernetes Audit Logs and integrating them with centralized platforms like Elasticsearch or Splunk.
Here’s a quick look at how Kubernetes aligns with specific regulatory mandates:
| Framework | Primary Requirement | Kubernetes Solution |
|---|---|---|
| PCI DSS Req 1 | Network segmentation | Network Policies, Calico, Cilium |
| PCI DSS Req 3 | Protect stored data | etcd encryption, Secrets management |
| PCI DSS Req 7/8 | Access control | RBAC, OPA Gatekeeper |
| PCI DSS Req 10 | Monitor access | Audit Logs, Falco runtime detection |
| NIST 800-53 AC | Least privilege | RBAC, Service Accounts |
| NIST 800-53 AU | Audit & accountability | Kubernetes Audit Logs |
| NIST 800-53 SC | Communications protection | Service Mesh (mTLS), Network Policies |
Policy as Code (PaC) tools like OPA Gatekeeper or Kyverno take compliance a step further by converting regulatory requirements into enforceable rules. For example, these tools can block non-compliant resources, such as containers running as root or unsigned images, directly in the DevSecOps pipeline. By catching violations early, organizations can prevent compliance issues from ever reaching production.
Mapping Compliance Controls to Kubernetes Components
Core Kubernetes Components and Compliance
Integrating compliance controls into Kubernetes components ensures security is embedded throughout the infrastructure. For example, the Kubernetes API server must enforce Role-Based Access Control (RBAC) and use TLS encryption (with --anonymous-auth=false) to align with HIPAA and least privilege principles. The numbers are concerning: 78% of organizations have publicly accessible Kubernetes API servers, violating fundamental NIST and CIS hardening standards.
By default, etcd stores Secrets in plaintext, which poses a compliance risk. To address this, enable EncryptionConfiguration or integrate an external vault solution like HashiCorp Vault to meet HIPAA and NIST SP 800-190 standards.
"Kubernetes Secrets are stored in plaintext in etcd by default, so encrypting etcd or using an external vault service like HashiCorp Vault may be necessary." – Medha Mehta, Pomerium
Secure communication between the controller manager and kubelets by implementing mTLS and using a dedicated Certificate Authority for etcd interactions. Additionally, explicitly set --kubelet-https=true to encrypt traffic between the API server and kubelets.
To enforce compliance at the pod level, ensure production manifests include settings like runAsNonRoot: true, allowPrivilegeEscalation: false, and readOnlyRootFilesystem. Use Pod Security Admission to enforce the Restricted Pod Security Standard, ensuring non-root execution and minimal Linux capabilities. Alarmingly, 58% of organizations have service accounts with unrestricted cluster-admin role bindings, highlighting the need for stricter controls.
Once the core components are secured, the focus shifts to implementing network-specific compliance measures.
Network Compliance Controls in Kubernetes
With component-level protections in place, network policies are essential for isolating workloads and protecting data in transit. Network Policies act as pod-level firewalls, directly supporting PCI DSS Requirement 1 and HIPAA transmission security requirements. Kubernetes’ default configuration allows unrestricted pod-to-pod traffic, which violates segmentation mandates. To address this, apply a deny-by-default network policy in every namespace, supplemented by specific allow-list exceptions.
"By default, Kubernetes allows all pod-to-pod traffic. This means if an attacker gets into one pod, they can reach almost everything else in your cluster." – Shauli Rozen, CEO & Co-founder, ARMO
For encrypting data in transit, consider using a service mesh like Istio, Linkerd, or Pomerium to enforce mTLS for internal cluster communications if your Container Network Interface (CNI) plugin lacks native encryption. For Kubernetes Ingress, configure TLS using secrets containing private keys and certificates, while restricting traffic to port 443 for secure termination. Additionally, block or filter workload access to the cloud metadata API (169.254.169.254) to prevent information leakage and use the DenyServiceExternalIPs controller to minimize the risk of man-in-the-middle attacks.
Namespaces play a crucial role in logical isolation, meeting requirements for HIPAA and GDPR data segregation. Create dedicated namespaces for workloads managing sensitive data, such as electronic Protected Health Information (ePHI), and avoid using the default namespace. To reduce the attack surface further, set automountServiceAccountToken: false for pods that don’t need API access.
Adding Compliance to DevSecOps Pipelines
After mapping compliance controls to Kubernetes components, the next step is to integrate these checks into CI/CD pipelines. This ensures that compliance is continuously upheld throughout the development lifecycle.
Vulnerability Scanning in CI/CD
Incorporating vulnerability scans at various stages of the pipeline helps catch and resolve issues early, saving time and resources. Start with Static Application Security Testing (SAST) during code commits and pull requests. This helps identify vulnerabilities like SQL injection or cross-site scripting within the source code. Tools such as SonarQube and Checkmarx can provide immediate feedback to developers.
During the build phase, use Software Composition Analysis (SCA) to check third-party libraries and open-source dependencies for known vulnerabilities. Tools like Trivy, Snyk, or Black Duck analyze dependency manifests and container images to flag CVEs before deployment. For container image scanning, integrate tools like Trivy, Clair, or Anchore directly into CI/CD platforms like Jenkins, GitLab CI, or GitHub Actions. This automation ensures that vulnerable images are blocked before they can be deployed.
"Fixing a flaw in production is far pricier and more embarrassing than catching it early. DevSecOps reduces the odds of a significant breach by systematically checking configurations, packages, and runtime behavior." – Wiz Academy
Dynamic Application Security Testing (DAST) plays a crucial role by simulating real-world attacks on running applications. This approach uncovers runtime vulnerabilities that static analysis might miss. Tools like OWASP ZAP or Burp Suite can test applications deployed on Kubernetes in staging environments before they handle production traffic. It’s worth noting that over 50% of Kubernetes security incidents in 2023 were caused by misconfigurations, many of which automated policy enforcement could have avoided.
These scanning processes feed directly into automated validations, ensuring that non-compliant artifacts are stopped before progressing further in the pipeline.
Automating Compliance Validation
Building on vulnerability scans, automated validation ensures only compliant code makes it to production. Implement fail-fast quality gates that halt deployments when critical CVEs or missing security settings (like runAsNonRoot: true) are detected.
Leverage Policy-as-Code (PaC) tools, such as Rego for OPA or YAML for Kyverno, to enforce compliance rules within the CI/CD pipeline. Tools like tfsec, Checkov, or kube-score can scan Infrastructure-as-Code files (e.g., Terraform, Helm charts, Kubernetes manifests) to catch misconfigurations early. A 2025 report highlighted that 80% of CI/CD workflows have overly permissive settings, posing significant supply chain risks.
Cryptographic attestations provide verifiable proof that artifacts have passed compliance checks. Tools like Sigstore’s Cosign can sign container images and Kubernetes manifests that meet security standards, creating a "Golden Thread" of evidence from build to production. Kubernetes admission controllers can then validate these attestations at deployment, ensuring only compliant workloads are allowed into the cluster.
"Verifiable compliance is not a document, but a queryable, real-time data stream." – Aleksandr Zakharchenko, Independent Researcher
Secrets management is another critical area to automate. Use git-secrets pre-commit hooks to block sensitive data like AWS keys or API tokens from entering repositories. Centralized vaults, such as HashiCorp Vault, can dynamically inject secrets during deployment. To unify results from various scanners, adopt the Static Analysis Results Interchange Format (SARIF), which consolidates outputs into a single, queryable format. For minor compliance issues, Kubernetes mutating webhooks can automatically apply missing security settings (e.g., readOnlyRootFilesystem), reducing manual effort.
In the next section, we’ll look at automated compliance monitoring and remediation to ensure continuous security.
Automating Compliance Monitoring and Remediation
Once you’ve integrated compliance checks into your CI/CD pipeline, the next challenge is maintaining that compliance as your Kubernetes cluster evolves. These environments are constantly changing – scaling up or down, reconfiguring, and encountering new vulnerabilities. Manual reviews quickly become outdated, drain resources, and can introduce errors.
"Manual compliance reviews are static and outdated the moment configurations change. They also consume significant operational time and introduce human error." – Plural.sh
Automation changes the game, turning compliance into an ongoing process rather than a periodic task. It ensures your cluster stays prepared with immutable audit trails that log every change and enforcement action. This approach not only reduces operational effort but also provides the real-time transparency that auditors and security teams need.
Setting Up Continuous Compliance Scanning
To achieve continuous compliance, you need tools that operate directly within your cluster – not just during the build phase. For example, deploying a Kubernetes Operator like Trivy Operator enables real-time monitoring for vulnerabilities, secrets, and misconfigurations beyond static CLI scans. For cluster-level hardening, kube-bench can automatically validate your control plane, node configurations, and RBAC settings against the CIS Kubernetes Benchmark. Scheduling kube-bench to run daily or after upgrades helps catch configuration drift and generates detailed reports outlining which checks passed, which failed, and how to fix them.
Admission controllers, paired with policy engines like OPA Gatekeeper or Kyverno, enforce compliance in real time by blocking non-compliant resources before they are deployed. For instance, the PodSecurity admission controller (available in Kubernetes 1.23+) can enforce Pod Security Standards, ensuring that containers don’t run as root, resources have proper limits, or the "latest" image tag isn’t used. Combining these tools with GitOps solutions like Argo CD or Flux ensures Git remains your single source of truth. Any manual changes outside Git are automatically flagged or reverted, creating an immutable record of configuration changes.
For a more comprehensive strategy, layer these tools together. Policy engines block non-compliant resources at deployment, scanners identify vulnerabilities in images and filesystems, and runtime monitors like Falco detect suspicious system calls or unauthorized API activity.
| Tool Category | Examples | Primary Function | When It Runs |
|---|---|---|---|
| Policy Engines | OPA Gatekeeper, Kyverno | Block non-compliant resources at admission | Deployment |
| Security Scanners | Trivy, Grype, Clair | Identify CVEs in images and filesystems | Build + Runtime |
| Benchmarking | kube-bench | Validate cluster against CIS standards | Runtime/Audit |
| Runtime Security | Falco | Detect live threats and anomalies | Runtime |
| GitOps Controllers | Argo CD, Flux | Prevent configuration drift | Deployment |
Track your progress with metrics like Mean Time to Detect (MTTD), Mean Time to Remediate (MTTR), and your overall Compliance Score – the percentage of resources meeting your defined standards. These metrics provide a clear picture of your compliance standing and help enable immediate, automated responses to deviations.
Automated Remediation Methods
Detecting compliance violations is only half the battle – automated remediation ensures they’re addressed quickly and effectively. Tools like Kyverno can inject missing security contexts (e.g., readOnlyRootFilesystem: true), labels, or sidecars into resource requests automatically. This process, called mutation, ensures that incoming resources adhere to your standards.
For runtime violations, quarantining becomes essential. For example, a pod running a vulnerable image or exhibiting suspicious behavior can be automatically isolated to a restricted namespace for further investigation. Additionally, GitOps-based rollbacks allow your controller to revert non-compliant changes to the last-known-good configuration stored in Git, keeping your cluster aligned with your desired state.
"By treating compliance as a software artifact, teams gain transparency, traceability, and a verifiable audit trail – forming a reliable foundation for Kubernetes compliance automation." – Plural.sh
To roll out automated compliance without disrupting workflows, start with an "Advisory" mode. In this mode, violations are logged but not blocked, giving teams time to adapt and address issues. Once policies are refined, switch to "Hard Mandatory" mode to enforce blocking.
Admission controllers can also help manage resources by enforcing CPU and memory limits on workloads, which prevents potential DoS attacks caused by malicious or compromised processes. Lastly, generating a Kubernetes Bill of Materials (KBOM) in CycloneDX format provides an accurate inventory of all control plane components, node versions, and add-ons. This inventory is invaluable for audits and incident response.
Choosing Kubernetes Compliance Tools
After establishing automated scanning and remediation strategies, the next step is selecting tools that can effectively implement these processes. Choosing the right compliance tools for your Kubernetes environment means identifying features that align with your regulatory requirements. A poorly chosen tool can lead to fragmented dashboards, excessive alerts, and wasted engineering resources.
Required Tool Capabilities
A solid compliance tool should include pre-built mappings to key industry standards like CIS Benchmarks, NIST, PCI DSS, SOC 2, and HIPAA. Without these, you’ll spend weeks manually translating regulatory requirements into Kubernetes controls. Tools that enable policy-as-code enforcement using formats like YAML or Rego can save significant time and effort.
Runtime threat detection is another must-have. Tools that use eBPF or syscall-level monitoring can catch behavioral anomalies and unauthorized actions that occur after deployment – issues static scans often miss. For example, Snowflake adopted Chainguard Containers while working toward FedRAMP High compliance. Under Brandon Sterne’s leadership, this move reduced vulnerabilities in their applications from hundreds or thousands to zero almost instantly.
"It’s a remarkable thing when you introduce Chainguard Containers and see the vulnerability count plummet. Watching various applications go from hundreds or even thousands of vulnerabilities down to zero overnight is a really powerful testament." – Brandon Sterne, Senior Manager of Product Security at Snowflake
Your tool should also support shift-left scanning, integrating with CI/CD pipelines to identify problems early in the development cycle. Automated auditing and reporting features are equally important, as they generate audit-ready logs and real-time telemetry without requiring manual input.
Supply chain security features – such as Software Bill of Materials (SBOM) generation, SLSA provenance tracking, and cryptographic image signing – are critical. Kubernetes clusters on platforms like AWS or Azure often face attacks within minutes of going live, making artifact integrity verification essential. Additionally, robust network policy enforcement is crucial to prevent lateral movement within your environment.
| Feature | Why It Matters | Impact on Compliance |
|---|---|---|
| Compliance Framework Mappings | Pre-built controls for industry standards | Cuts manual work from weeks to hours |
| Policy-as-Code | Automates compliance enforcement via YAML or Rego | Blocks non-compliant resources at admission |
| Runtime Detection (eBPF) | Monitors system calls and network activity | Identifies threats missed by static scans |
| Shift-Left Scanning | Analyzes IaC and container images in CI/CD | Prevents vulnerabilities before production |
| SBOM Generation | Provides an inventory of all components | Simplifies audits and incident response |
These features ensure compliance checks integrate seamlessly with your existing DevSecOps practices.
Integrating Tools With Existing Systems
Once you’ve identified the right capabilities, it’s essential to ensure your compliance tool integrates smoothly with your current DevSecOps setup. Start by confirming native Kubernetes support through mechanisms like Custom Resource Definitions (CRDs) and Admission Controllers. Tools should also integrate directly into CI/CD pipelines – whether you’re using Jenkins, GitLab CI, or GitHub Actions – to enable automated scans during every commit and deployment.
GitOps compatibility is another key consideration. Your tool should allow policies to be defined as code in version-controlled repositories, automatically syncing them across clusters. This approach ensures Git remains the single source of truth and provides an immutable audit trail. For instance, IDT Telecom used AccuKnox for eBPF-based runtime security and Zero Trust enforcement, effectively preventing lateral movement and privilege abuse in their Kubernetes environment.
"Choosing AccuKnox was driven by opensource KubeArmor’s novel use of eBPF and LSM technologies, delivering runtime security." – Golan Ben-Oni, Chief Information Officer at IDT Telecom
Unified dashboards are critical for consolidating compliance scanning and runtime security monitoring into a single interface. Relying on separate tools for different functions can increase operational complexity and the likelihood of missed alerts. Additionally, ensure the tool integrates with your identity and access management systems – such as LDAP or Microsoft Entra ID – for consistent user management and RBAC policies.
Set up targeted alerting to route security notifications directly to the DevOps teams responsible for specific applications or image layers. Launch new policies in "audit" or "dry-run" mode initially to log violations without blocking workloads, giving teams time to adapt before enforcing rules fully. With 55% of organizations reportedly delaying deployments due to Kubernetes security concerns, choosing tools that integrate seamlessly with your workflows can help avoid bottlenecks in your compliance program.
Conclusion
This guide highlights how integrating automation transforms Kubernetes compliance from a one-time audit into a continuous, proactive process. Staying compliant with Kubernetes requires constant adjustments to keep up with evolving threats, regulations, and technologies. The organizations that succeed are often those that embrace automation and develop a clear compliance strategy. By embedding compliance checks into CI/CD pipelines, teams can identify and fix misconfigurations early – saving time, cutting costs, and maintaining development speed.
Relying on manual compliance reviews can drain resources and slow down workflows. Automation, on the other hand, reduces Mean Time to Remediation (MTTR), eliminates the stress of last-minute audits, and makes compliance a regular part of operations. For example, about 50% of open-source Helm charts on Artifact Hub have security misconfigurations, which demonstrates the importance of continuous, automated enforcement.
Using Policy as Code ensures security standards are applied consistently, even across hundreds or thousands of clusters, without adding unnecessary complexity. Establishing key performance indicators like Mean Time to Detection (MTTD) and compliance scores – aligned with a DevSecOps framework – can help justify security investments to business leaders. Meanwhile, GitOps workflows provide an immutable audit trail and make it easier to roll back to compliant states when needed. These strategies not only simplify compliance but also improve operational efficiency.
The benefits go far beyond meeting regulatory requirements. A well-thought-out compliance strategy reduces technical debt, cuts infrastructure costs, and supports innovation by creating a secure environment where teams can move forward confidently. Instead of being a roadblock, compliance becomes a key driver for agility and growth.
FAQs
Where do I start mapping SOC 2, PCI DSS, or HIPAA controls to Kubernetes?
To align your Kubernetes environment with frameworks like SOC 2, PCI DSS, or HIPAA, start by identifying how their controls apply to your setup. Pay special attention to critical areas such as access management, data encryption, and audit logging.
Leverage tools like Policy as Code (PaC) with frameworks such as OPA Gatekeeper or Kyverno to automate compliance checks. These tools help enforce policies and ensure your configurations meet the required standards. Additionally, focus on creating a clear mapping of controls and maintain continuous monitoring to keep your Kubernetes environment in sync with these compliance requirements.
What should be blocked at admission vs detected at runtime?
Blocking at admission helps enforce security policies, like Pod Security Standards, to restrict pod privileges right from the start. On the flip side, runtime detection steps in to catch violations that go beyond these policies – things like unusual behavior or compromised workloads. Together, these methods play a crucial role in keeping Kubernetes environments secure.
How can I prove continuous compliance to an auditor without taking manual screenshots?
To maintain compliance effortlessly, ditch the manual screenshots and opt for automated tools. Solutions like audit trails, compliance reporting, and policy-as-code systems can handle the heavy lifting. These tools create tamper-proof, real-time documentation of your Kubernetes environment, giving auditors reliable and consistent compliance data at all times.