SIEM vs. Cloud-Native Threat Detection

Detecting threats in modern environments requires tools that match the pace of change. SIEM (Security Information and Event Management) systems and cloud-native threat detection tools offer different approaches to securing your infrastructure. Here’s the core difference: SIEMs are built for centralized log analysis, often relying on predefined rules, while cloud-native tools leverage AI and real-time monitoring to handle dynamic, cloud-based environments.
Key Takeaways:
- SIEM Strengths: Best for compliance-heavy industries, forensic investigations, and hybrid setups. SIEMs excel at long-term log storage and centralized data correlation but struggle with scalability and modern threats.
- Cloud-Native Strengths: Ideal for cloud-first businesses with ephemeral workloads. These tools prioritize real-time responses, AI-driven threat detection, and seamless integration with cloud platforms.
- Speed vs. Depth: SIEMs often detect threats after logs are processed (delayed). Cloud-native tools act in near real-time, reducing response times.
Quick Comparison:
| Feature | SIEM | Cloud-Native Threat Detection |
|---|---|---|
| Detection Method | Rule-based | AI and behavioral analytics |
| Primary Data Source | Log aggregation | Runtime and streaming telemetry |
| Response Speed | Delayed | Near real-time |
| Scalability | Hardware-dependent | Elastic, scales automatically |
| False Positives | High | Lower (AI-driven prioritization) |
| Deployment Time | Months | Hours or days |
| Cost Model | High upfront costs | Subscription-based |
Which is right for you? If you’re managing legacy systems or compliance-driven operations, SIEM might be a better fit. But if your infrastructure is cloud-heavy and fast-changing, cloud-native tools are better suited for the job. Dive into the full article for detailed comparisons and real-world examples.
SIEM vs Cloud-Native Threat Detection: Complete Feature Comparison
Cloud Security Podcast by Google – SIEM in the Modern Era
What is SIEM?
SIEM combines security information and event management into a single, unified platform. The concept, introduced by Gartner in 2005, describes a system designed to handle large volumes of event data from various sources like firewalls, servers, endpoints, cloud applications, and network devices. It processes this data by normalizing it into a standard format and then applies predefined rules and algorithms to correlate events across systems. For instance, a SIEM might detect a compromised account login and link it to unusual network activity occurring at the same time, triggering a high-priority alert. By storing logs over extended periods, SIEM solutions also enable forensic investigations, helping teams reconstruct past incidents and trace the paths attackers took.
"SIEM solutions help organizations recognize and address potential security threats and vulnerabilities before they have a chance to disrupt business operations."
SIEM systems provide essential tools for compliance reporting, forensic analysis, and real-time monitoring through automated log analysis. When it comes to compliance, they streamline the creation of reports for regulations like GDPR, HIPAA, PCI-DSS, and SOX. Additionally, centralized dashboards offer security teams a comprehensive view of their organization’s security posture. These capabilities set the foundation for understanding the key features that make SIEM indispensable.
Core Features of SIEM
SIEM systems are built around centralized log collection, standardized correlation rules, and automated compliance reporting. They gather data from both on-premises systems and cloud environments, then parse and standardize it to facilitate effective analysis. Correlation rules play a critical role in identifying threats by analyzing patterns across multiple data sources. This helps detect suspicious activities that might seem harmless when viewed individually.
Modern SIEM solutions are also integrating AI and User and Entity Behavior Analytics (UEBA) to establish behavioral baselines. These tools identify anomalies that deviate from typical patterns, even when they don’t match known attack signatures. Furthermore, SIEM platforms often include pre-built templates for regulatory compliance, automating the collection and analysis of logs to meet audit requirements.
Limitations of SIEM
Traditional SIEM systems often produce an overwhelming number of alerts, leading to alert fatigue. Maintaining on-premises SIEM hardware requires specialized engineers to handle configurations, updates, and ongoing maintenance. Moreover, these systems frequently encounter scalability challenges tied to physical infrastructure, making it difficult to keep up with the increasing volumes of data.
"Traditional SIEMs require analysts to collate data from various sources to make sense of the attack timeline. This can be time-consuming and requires special expertise."
Another challenge lies in adapting to modern threats. Static correlation rules often fail to detect more sophisticated, stealthy attacks that don’t follow predictable patterns. This is especially concerning given that the average breakout time for cyber intrusions has dropped to just 48 minutes – and in some cases, attackers can move laterally within 51 seconds. Keeping SIEM rules updated to address these rapidly evolving threats becomes a labor-intensive task. While SIEM tools are invaluable for compliance and forensic analysis, their reliance on static methods makes them less effective in navigating today’s fast-changing threat landscape.
What is Cloud-Native Threat Detection?
Cloud-native threat detection is designed to protect dynamic cloud environments where traditional, fixed network defenses fall short. Unlike static firewalls or rigid perimeters, these tools are built for highly flexible setups involving containers, microservices, and serverless functions that constantly scale up or down. By leveraging AI, machine learning, and behavioral analytics, they detect threats in real time, focusing on identity, workload security, and continuous monitoring instead of outdated network-based strategies. This modern approach addresses the gaps left by static SIEM rules.
Cloud environments operate fundamentally differently from traditional data centers, which makes their security needs unique. For instance, static firewalls can’t protect applications spread across multiple clouds or ephemeral resources that may only exist for a few seconds. Cloud-native tools tackle these challenges by monitoring activity at the kernel level using technologies like eBPF (Extended Berkeley Packet Filter). This allows them to gather low-level behavioral data without slowing down performance. Additionally, they employ natural language processing to analyze scripts in languages like Bash and Python, detecting malicious intent even in threats that don’t match established patterns.
In 2025, BigCommerce adopted Sysdig’s runtime security system under CISO Dan Holden. The result? A detection time of under 2 seconds and a 20% increase in vulnerability identification, showcasing a level of speed and accuracy that traditional SIEM solutions couldn’t match. Similarly, Vertiv shifted to Google Security Operations, logging 22 times more data while cutting investigation times in half, highlighting the efficiency gains of this approach.
Core Features of Cloud-Native Tools
Cloud-native tools are built to provide real-time detection and response. They rely on anomaly detection and automated responses, establishing behavioral baselines for users and entities. When deviations occur – like compromised service accounts or unusual lateral movement – these platforms flag them, catching threats that human analysts might overlook. Many of these tools use thousands of detectors aligned with the MITRE ATT&CK framework to pinpoint specific attack behaviors, such as privilege abuse or stealthy execution.
Automation plays a key role here. These systems integrate seamlessly with SOAR platforms, enabling instant responses to threats. For example, they can isolate compromised workloads or revoke risky IAM permissions automatically. At Google, about 97% of security events are handled through automated processes rather than manual reviews. This speed is critical since attackers can exfiltrate sensitive data faster than traditional systems can respond. Moreover, these tools maintain a continuous inventory of all cloud assets, complete with creation history, enabling programmatic queries of infrastructure.
Advantages Over SIEM
Cloud-native tools don’t just offer advanced features – they deliver measurable improvements over SIEM systems. Organizations using these solutions report 79% fewer false positives and 44% lower costs compared to legacy systems. For instance, in March 2024, Danfoss implemented Microsoft Sentinel under Director Chunqui Chen. By ingesting logs from 20 applications and thousands of devices, the company reduced time spent on false positives and repetitive tasks by 50%–60%, achieving significant cost and efficiency gains.
Scalability is another major strength. Unlike traditional SIEMs that struggle to adapt to the elastic nature of cloud environments, cloud-native tools scale automatically alongside infrastructure. Whether dealing with hundreds or millions of instances, these systems adjust seamlessly. Continuous updates powered by machine learning further enhance their effectiveness, reducing breach risks by 35% and cutting remediation times from hours to minutes.
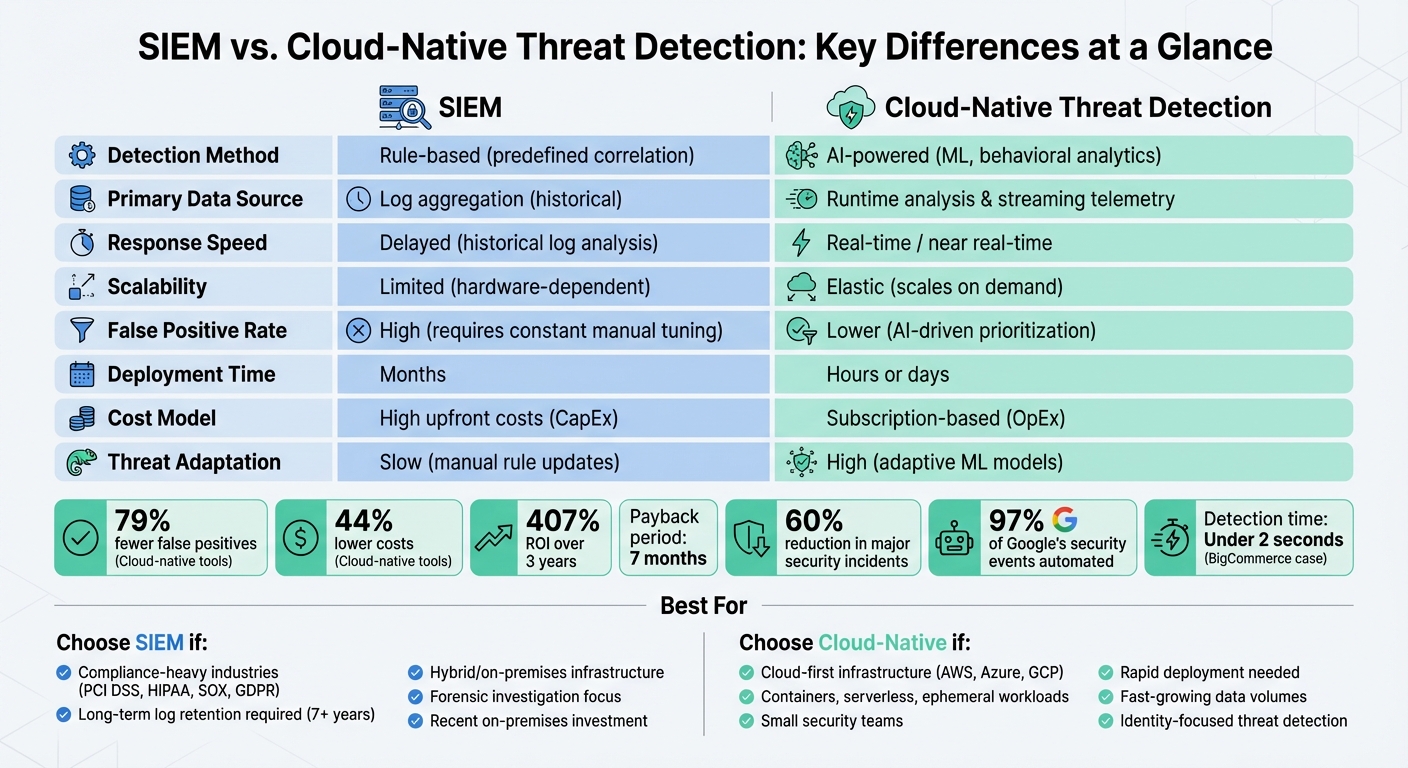
Key Differences Between SIEM and Cloud-Native Threat Detection
The main distinction between SIEM and cloud-native tools lies in how they approach threats. Legacy SIEMs depend on predefined correlation rules, while cloud-native tools leverage AI and behavioral analytics to spot anomalies. This difference highlights the shift from reactive to proactive threat detection.
SIEMs are built around historical log aggregation. On the other hand, cloud-native platforms prioritize runtime analysis and streaming telemetry. This shift is crucial in modern infrastructures that are distributed, immutable, and often short-lived.
Comparison Table: SIEM vs. Cloud-Native
| Feature | Legacy SIEM | Cloud-Native Threat Detection |
|---|---|---|
| Detection Method | Rule-based (predefined correlation) | AI-powered (ML, behavioral) |
| Primary Data Source | Log aggregation (historical) | Runtime analysis & streaming telemetry |
| Response Speed | Delayed (historical log analysis) | Real-time / near real-time |
| Scalability | Limited (hardware-dependent) | Elastic (scales on demand) |
| False Positive Rate | High (requires constant manual tuning) | Lower (AI-driven prioritization/triage) |
| Threat Adaptation | Slow (manual rule updates) | High (adaptive ML models) |
| Deployment | Slow/complex (months) | Fast (hours or days) |
"Legacy solutions have complex workflows and lack cloud-specific context, making them inadequate for the scale and complexity of cloud environments." – Elastic
This breakdown highlights how detection speed is a key factor that separates these two approaches.
Detection Speed and Effectiveness
Speed can make or break security efforts. Traditional SIEMs often produce alerts well after an incident has occurred – logs must first be ingested, processed, and analyzed before any issues are flagged. In contrast, cloud-native tools rely on streaming telemetry, enabling real-time visibility and quicker responses.
For instance, in January 2025, Google’s detection and response team, led by Director Tim Nguyen, managed the world’s largest Linux fleet and 180,000 employees using a cloud-native detection engine. By automating 97% of event generation through "hunts" and streaming logs into a cloud data warehouse, they slashed attacker dwell time from weeks to just a few hours.
The difference in effectiveness is clear in daily security operations. In 2021, 90% of businesses reported struggling to handle the overwhelming volume of security alerts they received each day. Legacy SIEMs often generate high false positive rates, requiring constant manual adjustments. Meanwhile, cloud-native tools use automated enrichment and contextual prioritization to cut through the noise. For environments where workloads are ephemeral – spinning up and shutting down in mere seconds – relying on historical log analysis isn’t just slow; it’s impractical for modern operations.
Deployment, Scalability, and Cost Considerations
When comparing SIEM and cloud-native tools, the most striking contrasts emerge in how they handle deployment, scaling, and costs. These factors play a pivotal role in determining which solution aligns best with your business needs.
Deployment Complexity
Traditional SIEMs involve lengthy and intricate deployments. From procuring hardware to configuring complex software and ensuring ongoing maintenance, the process can take months. On the other hand, cloud-native tools offer a much faster alternative, often allowing setup within hours. These tools eliminate the need for infrastructure management, enabling teams to start ingesting logs and identifying threats almost immediately. Thanks to agentless integration, cloud-native tools can collect data directly from cloud environments without requiring additional software installation on customer systems.
With cloud-native solutions, the infrastructure is managed by the vendor, freeing security teams to focus on their primary tasks – detecting and mitigating threats – rather than dealing with system administration. This distinction is especially beneficial for smaller teams or organizations with growing infrastructures.
Now, let’s see how these deployment differences impact scalability and long-term maintenance.
Scalability and Maintenance
Scaling legacy SIEMs can be a resource-intensive process. Adding capacity often means purchasing more hardware, which not only incurs high costs but also requires manual intervention. In contrast, cloud-native platforms are designed to scale elastically. They can handle increasing workloads on demand without compromising performance. For example, Google’s cloud-native infrastructure supports petabyte-scale data processing and offers up to 12 months of instantly searchable "hot" retention.
The advantages of scalability extend beyond performance. According to IDC, organizations that transition to modern security operations platforms report an average three-year ROI of 407% and a payback period as short as seven months. Additionally, enhancing SIEM capabilities through modernization has been shown to reduce the likelihood of a major security incident by 60%.
These scalability improvements also have a direct impact on costs, which we’ll explore next.
Cost Implications
The cost structures of legacy SIEMs and cloud-native platforms are fundamentally different. Legacy SIEMs come with hefty upfront expenses, including hardware, licensing, and operational costs like power, cooling, and dedicated personnel. In contrast, cloud-native solutions use a subscription-based pricing model, which eliminates the need for hardware investments and simplifies budgeting.
| Cost Factor | Legacy SIEM | Cloud-Native |
|---|---|---|
| Initial Investment | High CapEx (hardware + licensing) | Low (subscription-based) |
| Scaling Costs | Requires new hardware | Elastic, pay-as-you-grow |
| Maintenance | Power, cooling, dedicated staff | Vendor-managed infrastructure |
| Pricing Model | Upfront + ongoing OpEx | Consistent subscription fees |
| Hidden Costs | System administration, patching | Minimal operational overhead |
For businesses expecting significant data growth, these cost differences become even more pronounced. Legacy systems often face performance limitations that demand costly hardware upgrades. Meanwhile, cloud-native platforms seamlessly adapt to growth without performance degradation. This scalability is critical for smaller teams, where resources are often stretched thin. In fact, 73% of SME security professionals report missing high-priority alerts due to limited staff and time. In such cases, removing the burden of infrastructure management isn’t just a convenience – it’s a necessity for maintaining effective security operations.
sbb-itb-f9e5962
Incident Response and Integration Capabilities
When it comes to incident response and integration, traditional SIEMs and cloud-native platforms take very different approaches. Traditional SIEMs are primarily focused on alerting – they gather logs, correlate events, and notify security analysts, leaving the investigation and response to manual processes. In contrast, cloud-native tools emphasize automated mitigation, acting directly on the infrastructure. For instance, if a cloud-native platform identifies a misconfigured S3 bucket or an overly permissive security group ACL, it can automatically fix the issue by leveraging direct API integration with the cloud provider.
Alerting vs. Automated Mitigation
The workflows for responding to threats vary greatly between these two systems. Traditional SIEMs often rely on SOAR platforms to introduce automation. These platforms use structured playbooks – like Azure Logic Apps – to coordinate actions across multiple third-party tools. While effective, this method requires analysts to switch between systems to fully investigate and respond to threats. On the other hand, cloud-native platforms simplify the process by enabling "one-click" remediation straight from the alert interface.
The impact of automation is striking. Google, for example, has reduced threat dwell time from the industry average of weeks to just hours. According to Tim Nguyen, Director of Detection and Response at Google, 97% of their security events are generated through automated searches, which are then handed off to human analysts with detailed risk scores and investigation guidance.
"Roughly 97% of our events are generated through automated ‘hunts’, and then presented to a human along with a risk score and details about where to investigate." – Tim Nguyen, Director, Detection and Response, Google
Cloud-native tools further enhance their capabilities by using agentless ingestion through Cloud Service Provider APIs. This approach allows them to monitor transient resources like containers and serverless functions – something traditional SIEM agents often struggle to handle.
Integration with Cloud Infrastructure
In addition to automated responses, cloud-native platforms offer seamless integration with cloud services. These tools connect directly with AWS CloudTrail, Azure Activity Logs, and GCP APIs to maintain real-time inventories of cloud assets. Unlike traditional SIEMs, which rely on log collectors and connectors that can lag behind dynamic cloud environments, this native integration ensures up-to-date monitoring of ephemeral resources. The benefits are clear: one organization reported cutting their detection and investigation time from 2 hours to just 15–30 minutes after adopting a cloud-native SIEM. Similarly, Microsoft Sentinel users saw a 79% drop in false positives and a 35% lower likelihood of data breaches with integrated cloud-native security solutions.
Comparison Table: Response and Integration
| Feature | Traditional SIEM | Cloud-Native Threat Detection |
|---|---|---|
| Primary Response | SOAR playbooks & ticketing (e.g., Jira, ServiceNow) | Direct API-based auto-remediation |
| Automation Focus | Workflow orchestration across multiple tools | Infrastructure configuration & resource management |
| Cloud Compatibility | Requires connectors/agents; struggles with ephemeral assets | Native CSP API integration; agentless monitoring |
| Investigation Context | Log-based correlation and timeline reconstruction | Graph-based analysis of identities and attack paths |
| Recovery Time | Days to weeks (manual processes) | Hours (automated response) |
For containerized environments, cloud-native platforms go a step further by providing code-to-cloud lineage. This feature links runtime threats back to their origin in the CI/CD pipeline, making it possible to identify the development team responsible for the issue. Traditional SIEMs, operating outside the cloud provider’s ecosystem, simply cannot match this level of integration.
When to Choose SIEM
Traditional SIEM systems are a strong fit for organizations operating in industries with strict regulations, such as PCI DSS, HIPAA, SOX, GDPR, FedRAMP, and DORA. These industries often require centralized log retention, long-term data storage (sometimes up to seven years), and a robust on-premises infrastructure. As Christopher Beier, Principal Product Marketing Manager at Sumo Logic, explains, “For many organizations, compliance is the first reason SIEM is purchased. Frameworks like PCI DSS, HIPAA, SOX, GDPR, FedRAMP, and DORA all require centralized log retention and reporting”. Traditional SIEM solutions are specifically designed to meet these compliance needs by securely storing security log data for extended periods.
Organizations with strict data sovereignty requirements or those needing to retain sensitive data on-site often rely on SIEM for its on-premises control. For teams that already possess in-house response capabilities, SIEM provides a powerful tool for correlating logs across various domains without incurring additional cloud costs. This is especially useful for forensics-driven organizations that need to reconstruct attack timelines and preserve evidence trails. These technical strengths also contribute to a predictable total cost of ownership, making SIEM a practical choice for organizations with stable data volumes.
Companies that have recently made significant investments in on-premises infrastructure may find SIEM more cost-effective compared to transitioning to a subscription-based cloud model. As Heidi Willbanks from Exabeam points out, a thorough total cost of ownership (TCO) analysis often tips the scales in favor of SIEM in such scenarios.
SIEM also shines in hybrid environments, where not all security data resides in the cloud. Many legacy systems lack modern APIs and aren’t designed to integrate seamlessly with cloud-based architectures. In these cases, SIEM’s established collectors offer dependable integration, serving as the single source of truth for the entire security ecosystem. This reliability makes SIEM indispensable for organizations managing both legacy and modern systems.
When to Choose Cloud-Native Threat Detection
Cloud-native threat detection is ideal for organizations that operate primarily in cloud environments with dynamic, ever-changing infrastructure. If your workloads rely on containers, serverless functions, or temporary instances that appear and disappear throughout the day, traditional SIEM agents often can’t keep up. As Anton Chuvakin, Security Advisor at Google Cloud, points out:
"Cloud is usually distributed, often immutable, ephemeral, API driven, centered on identity layer, and automatically scalable. All these affect detection for the cloud environment".
This flexibility is especially helpful for teams with limited resources. For smaller security teams, cloud-native tools are a game-changer. They eliminate the need to manage hardware, apply patches, or maintain complex infrastructure. Instead, vendor-managed services allow your team to focus on responding to threats rather than being bogged down by system maintenance. Another major advantage is the speed of deployment – cloud-native solutions can be up and running in just a few hours or days, unlike the months it often takes to implement traditional SIEM systems. This speed is crucial when immediate visibility into security events is required. On top of that, these tools handle rapid data growth effortlessly.
If your organization is experiencing a surge in data, cloud-native tools are worth considering. They scale elastically, avoiding the performance issues or costly hardware upgrades that legacy SIEM systems often demand. This scalability is essential for keeping up with the fast-paced nature of cloud operations, ensuring that threat detection remains effective as your infrastructure grows.
Cloud-native tools also excel at addressing identity-focused threats. Modern cloud attacks increasingly target elements like IAM permissions, API keys, and service accounts, rather than relying on traditional network-based vulnerabilities. These tools are specifically designed to analyze IAM configurations and API activity in real time, making them well-suited for today’s cloud security challenges.
Cost is another significant advantage. Cloud-native solutions eliminate the need for large upfront investments, offering predictable subscription models instead. This makes them especially appealing for businesses without major on-premises infrastructure. Santosh Krishnan, General Manager of Elastic Solutions, highlights this benefit:
"Combining CDR and AI-driven security analytics can reduce tool fragmentation and centralize data, empowering the security teams to protect their cloud environments effectively. This comprehensive approach maximizes efficiency, lowers the total cost of ownership (TCO), and alleviates the burden on security teams".
In short, cloud-native threat detection offers a modern, scalable, and cost-effective approach for organizations navigating today’s complex cloud environments.
Conclusion: Choosing the Right Solution for Your Business
Based on our in-depth comparisons of functionality, cost, and response capabilities, the right choice ultimately comes down to how well the solution fits your infrastructure and operational needs.
The decision between SIEM and cloud-native threat detection isn’t about finding the “better” technology – it’s about selecting the one that aligns with your specific setup. If your operations are primarily on-premises and governed by strict regulatory log requirements, a traditional SIEM might still be the best fit. On the other hand, if your workloads are spread across platforms like AWS, Azure, or GCP, and you’re using containers or serverless functions, cloud-native tools are specifically designed for those environments.
Growth potential is a key factor here. If your organization anticipates significant expansion, cloud-native solutions offer the scalability you’ll need without the performance issues or hardware expenses that often accompany legacy systems. For example, Google Security Operations reports a 407% return on investment over three years, with a payback period of just seven months. This underscores the financial benefits of avoiding the hidden costs of traditional SIEM systems. Additionally, if your security team is already stretched thin, cloud-native platforms can help by handling infrastructure maintenance, patching, and updates, allowing your team to focus on more critical tasks like threat detection and response. This is especially important given the constantly evolving tactics of cyber attackers.
For businesses operating across multiple cloud providers, cloud-native platforms simplify management and improve efficiency. And if your priority is detecting advanced, unknown threats, the AI, machine learning, and behavioral analytics capabilities of cloud-native tools surpass the rule-based correlation methods used by legacy systems. Modern platforms can even reduce the likelihood of a major security incident by 60%, a statistic that carries significant weight in any risk assessment.
Take a close look at your infrastructure, growth plans, and team capacity. If you’ve recently invested heavily in on-premises hardware, a detailed total cost of ownership analysis is crucial before making any changes. However, for new deployments or modernization efforts, cloud-native solutions are the stronger choice. The security landscape is evolving rapidly – your tools need to evolve with it.
FAQs
What makes cloud-native threat detection tools more scalable than traditional SIEM systems?
Cloud-native threat detection tools offer a level of scalability that’s hard to match, thanks to their use of elastic cloud infrastructure. Instead of relying on fixed, on-premises hardware, these platforms dynamically adjust compute, storage, and query capacity as data volumes increase. What does this mean in practice? Smooth performance without the headaches of manual upgrades or the inefficiency of over-provisioning. Many of these tools are built on serverless or SaaS architectures, which also means organizations only pay for what they actually use – no more, no less.
Compare this to traditional SIEM systems, which depend on pre-sized hardware designed to handle peak loads. This approach often results in one of two problems: performance bottlenecks or the high costs of over-provisioning. Cloud-native tools remove these roadblocks entirely. They grow effortlessly alongside your data, aligning costs with actual usage. And for engineering teams, this flexibility is a game-changer. Instead of wrestling with infrastructure, they can focus their energy on driving innovation forward.
How does the cost of cloud-native threat detection compare to traditional SIEM solutions?
Switching to a cloud-native threat detection platform can transform the way organizations handle expenses, replacing hefty upfront costs with a manageable, subscription-based pricing model. Traditional SIEMs often demand significant investments in on-premise hardware, licensing fees, and the staff needed to scale operations – expenses that can easily drive annual budgets into six figures before even starting to process logs.
Cloud-native platforms, on the other hand, operate on a usage-based pricing model. Typically, they charge $10–$20 per asset per month and can lower log ingestion costs by 30–50% through selective forwarding. For U.S. companies, this means monthly costs adjust with usage. For instance, managing 1,250 assets could cost $12,500–$25,000 per month.
This model eliminates the hassle of hardware depreciation, reduces the need for dedicated maintenance teams, and aligns expenses with actual growth in cloud usage. It’s a more flexible and predictable way to manage costs, making budgeting simpler and easier to justify.
How do cloud-native tools differ from traditional SIEMs in real-time threat detection?
Cloud-native tools shine when it comes to real-time threat detection. By processing security events as they happen, these tools use cloud APIs and serverless technologies to instantly provide context about workloads, identities, and configurations. They automatically scale to manage vast amounts of streaming data, ensuring smooth performance even in highly dynamic environments. Plus, they generate alerts in near real-time, enabling quicker responses to potential threats.
In contrast, traditional SIEMs often rely on batch log collection and scheduled processing, which can lead to delays and make it harder to keep up with the scalability demands of modern cloud infrastructures. They also tend to lack the built-in cloud context needed to identify fast-evolving attacks. Cloud-native solutions, designed to align with modern infrastructures, offer the agility and efficiency that traditional SIEM setups struggle to match – all without the burden of extensive maintenance.